CyberLAC Cyber Security Assessment Services
Unparalleled security monitoring resources to proactively safeguard your OT environment, identify risks, and swiftly respond to potential threats.
Cyber Security Assessment Services
Our cyber security assessment services will provide a thorough risk, threat, and vulnerability assessment to ensure your organization's security. We take a multidisciplinary approach to security to mitigate risks from data and the physical environment. The human element in relation to the role of technology
Our cybersecurity risk assessment and IT security risk assessment services investigate and address known security gaps' root causes and risk factors in a company's technology infrastructures and employee training. This procedure is critical for maintaining an effective cyber security strategy.
Cyber Security Assessment Features & Benefits
Information Security Assessment
Data Governance Assessment
Technical Security Control Testing
Compliance Assessment
Policy Review and Assessment
Third-Party Risk Assessment
IT Risk Assessment
Application Security Assessment
Malicious Code Analysis
Business Continuity Assessment
Vulnerability Assessment
Penetration Testing
Phishing Assessment
Capabilities
Our broad cybersecurity knowledge and deep industry expertise allow us to develop next-gen cybersecurity services to protect your business, from end to end.
-
While simulating life-like cyberattacks, our ethical hackers perform cyber security penetration testing, try to get privileged access to corporate digital assets, and evaluate the risks related to discovered security loopholes.
* Application Assessment Service
* Vulnerability Assessment
* Penetration Testing
* Phishing Testing
* Compliance Assessments
* Cloud Security Assessments
-
When you outsource your security operations to CyberSecOp Managed SOC service, you can realize the full benefits of a SOC without investing the time or resources required to build and maintain one. Our managed SOC team comprises certified risk professionals focused on Managed Detection and Response (MDR), SIEM, DLP, DNS Filtering, AEP, and CASB Managed services.
Managed Detection and Response
* Incident Notification
* Managed Threat Hunting
* Malware Analysis
* Phishing Testing
* Incident Response
-
CyberSecOp is an award-winning cybersecurity firm with unrivaled expertise in delivering SOC as a Service.
Our managed security global security operations centers (SOCs) service can assist you in gaining visibility, security, and control over your industrial operations. Proactive monitoring throughout the security ecosystem maximizes investment value while balancing outsourced expertise and in-house teams.
Enhance Cybersecurity Monitoring
* Data Breach Prevention
* Ransomware Detection
* Data Loss Prevention
* Dark Web Monitoring
* Attack Surface Monitoring
-
Cyber security management services, such as compliance and risk management, managed SOC, managed detection and response, vulnerability management, and managed incident response retainer services. Our managed security service team will manage all things security.
* Managed Detect and Respond Services
* Cyber Threat Exposure Management Consulting
* Data Protection Management Consulting
* Third-Party Risk Management Consulting
* Cloud Security Sustainment Consulting
* Digital Identity Management
* Managed Privacy Consulting
* Supply Chain Security Management
* Security Operations & Cybersecurity Consulting
-
Our Cyber Incident Response services consultants can assist with forensic, cyber security risk mitigation, threat intelligence, threat hunting, and compliance efforts.
* Strategy and Planning Consulting
* Tabletop Exercises
* Ransomware Negotiation & Payment
* Cyber Emergency Breach Response
* Digital Cyber Forensics and Litigation Support
* Compromise Assessments Services
* Cyber Threat Hunting
* Business Continuity / Business Resiliency
* Postmortem Report
-
Our comprehensive approach to infrastructure and cloud security safeguards them from the inside out, unlocks value, and increases your return.
* Incident Notification
* Managed Threat Hunting
* Malware Analysis
* Phishing Testing
* Incident Response
We’ve Helped Identify And Defend Against Some Of The Highest-Profile Cybersecurity Attacks.
.
Cyber Security Assessment Services Overview
Our Cyber Security assessment services provide the following security assessment services: vulnerability assessment, penetration test assessment, phishing simulation assessment, red team assessment, compliance audit/assessment, white/grey/black-box security assessment, data risk assessment, threat assessment, and bug bounty program assessment services. CyberLAC IT security risk assessment services provide an in-depth insight into your cyber security risks and threats. Our cyber security assessment and compliance services help your business make the best decisions regarding capital, resource, and regulatory compliance costs for both current and future information assets.
What is a cyber security assessment?
Cybersecurity Assessment analyzes each system level, response strategies, training strategies, business continuity strategies, etc. This comprehensive analysis and response create cyber security protocols evolving to meet threats.
Security gaps in the system can be identified and filled with proper training, software patches, or network reorganization. At the same time, a response strategy can be put in place to reduce the effect of an attack or system breach. Creating an effective security system must be tested, analyzed, and altered where needed as situations change and new risks arise. CyberLAC Cyber security assessment services analyze and redress the causes and risk factors of your organization's known and unknown security gaps.
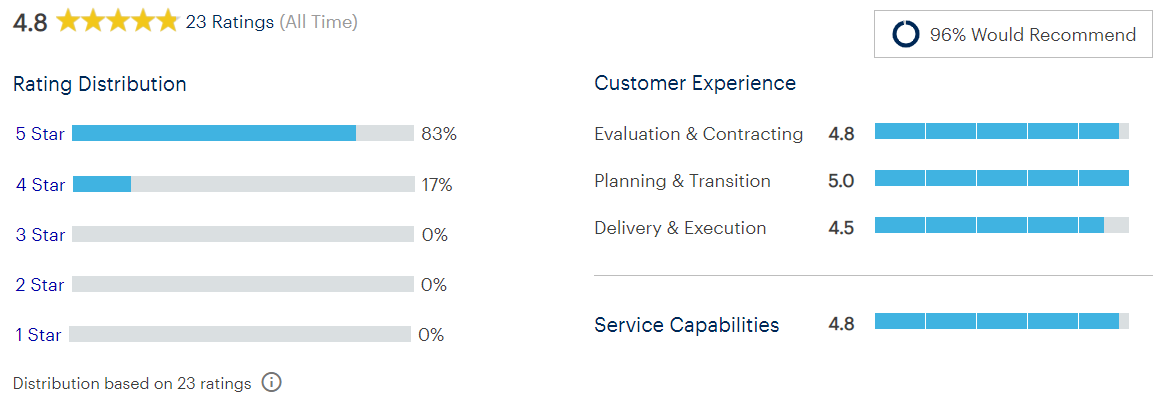
What people are saying
Award-winning Cyber Security Consulting Firm
Our Security Operations Center (SOC) aids your information security team monitor and analyzing an organization’s security posture on an ongoing basis. The SOC team’s goal is to detect, research, and respond to cybersecurity incidents using a combination of technology solutions and robust processes.

Business Integrated Cybersecurity Services